- Zscaler Macos Big Sur
- Zscaler Download For Windows 10
- Zscaler App Download Windows 10
- Zscaler Mac Install
- Zscaler Client Connector Download
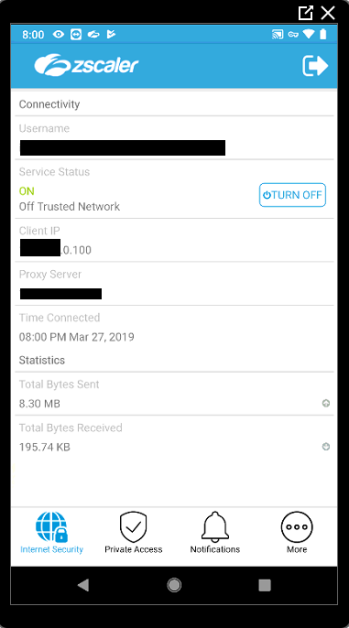
This section provides the whitelisting rules for Zscaler Client Connector: If your organization uses GPO to push policies to both Windows 64-bit and Windows 32-bit systems, then add the Whitelisting instructions for both the versions in your GPO policy. Zscaler Client Connector 1.5 (or later) doesn't support the fciv.exe file. Zscaler is enabling secure digital transformation by rethinking traditional network security, and empowering enterprises to securely work from anywhere.
The thoughts and opinions in this post are my own and do not necessarily reflect those of Zscaler.
In this guide, we'll walkthrough how to configure Microsoft Intune from scratch and use it to deploy the Zscaler Client Connector agent (ZCC) - formerly known as Zscaler Client Connector (ZCC).
Due to length, I've split this into two posts (the orginal was over 8000 words):
- This post covers deployment on Windows and macOS.
- The other post, available here, covers iOS and Android.
I suggest you use the Table of Contents to jump to the section that you need.
According to Microsoft:
Microsoft Intune is a cloud-based service that focuses on mobile device management (MDM) and mobile application management (MAM).
With Intune, you can:
- Set rules and configure settings on personal and organization-owned devices to access data and networks.
- Deploy and authenticate apps on devices – on-premises and mobile.
- Be sure devices and apps are compliant with your security requirements.
In order to access Intune, you need to have either a Microsoft 365 or Enterprise & Mobility E3/E5 subscription. If you're using a free Azure account, you'll need to sign up to a trial, or pay per user (which can get costly).
Scott Bullock of Zscaler (@scottyb) has posted a great 10 minute video in their community forum that runs through the user experience of enrolling a fresh Windows 10 device into Intune. ZCC is automatically pushed out and transparently authenticated for both ZIA and ZPA.
When adding an app to Intune, you'll be prompted to allocate the groups of users (or devices) that the app will be rolled out to. Hence before beginning, ensure you have the users of Zscaler inside of an AD or Azure AD group that you can assign the Zscaler Client Connector app to.
Depending on whether you want the ZCC app to be mandatory or optional for certain groups of users, you may want to divide your users into two groups:
- The users to which the app is MANDATORY. Any user in this group will have the app automatically pushed out to them.
- The users to which the app is OPTIONAL. The app will not be automatically pushed for users in this group, allowing them to go to the Company Portal and download it themselves if they choose.
In my examples below, I have 3 groups:
| Group | Description |
|---|---|
| ZIA_Entitlement | This is the group of all users that are entitled to use Zscaler Internet Access (ZIA) |
| ZPA_Entitlement | This is the group of all users that are entitled to use Zscaler Private Access (ZPA). In my case, this is a subset of users from the ZIA_Entitlement group as I might not want to roll ZPA out to every user in the organization. |
| Zscaler - Mandatory | This group contains every user in the organization to which the ZCC app will be automatically rolled out to. Ie: The majority of users from the above two groups. If this is your organization, you might include the whole org in this group, except select users (eg: some from IT) for which the app will be optional. |
We'll be using the Microsoft Endpoint Manager console (MEM) to orchestrate Intune. You can log in using the same Azure Portal credentials here: https://endpoint.microsoft.com
Zscaler Macos Big Sur
(Optional) Setting the MDM Authority
If you're using an existing Office 365 account and have been using the Office 365 MDM, you'll need to change the MDM authority from Office 365 to Intune. This Microsoft help article will guide you through it.
This section will cover deploying ZCC onto Windows using Intune.
1. Download the Zscaler Client Connector MSI
To start you'll need the .MSI installer for ZCC from the Zscaler Client Connector Portal. Log into the portal (either through ZIA or ZPA) and navigate to Administration > Zscaler Client Connector Store.
In the Windows panel, download the MSI for the latest 2.X.X version. Do not use the older 1.X.X releases.

2. Add a new Line-of-Business App
Add a new Line of Business (LoB) App
Back in the Apps menu of the MEM portal, navigate to Apps > All Apps > Add. In the panel that appears, scroll to the bottom and under the Other heading, select Line-of-business app.
When prompted to select an app package file, upload the MSI of the Zscaler Client Connector you downloaded above and click OK.
Customize the App Details
Fill in the required details about the app:
| Field | Content |
|---|---|
| Name | Enter Zscaler Client Connector 2.X.X.X (where 2.X.X.X is the version number of the app - this will help you distinguish what version is being distributed by Intune) |
| Description | Enter Zscaler Client Connector |
| Publisher | Enter Zscaler, Inc |
| Ignore app version | Set to Yes. ZCC will automatically update itself once deployed, so Intune can safely ignore the version the user has installed after deployment. |
| Category | (Optional) Select an app category to allocate the Zscaler Client Connector to. |
| Command-line arguments | See below. |
For the Command-line arguments section, enter the following (substituting in your own cloud and domain info):
Important!
- When entering the cloud name, DO NOT enter the .net at the end. Eg: zscalertwo.net should be entered as
zscalertwo - All command-line arguments should be on a single line with a space separating them. Do not linebreak each argument or they will fail.
Command-line arguments can be used for each platform to customize the install. For example, STRICTENFORCEMENT can be used to block access to the internet until your users enroll in the Zscaler Client Connector.
For a list and description of all the MSI customization options, scroll down to point #5 in this help article.
Click Next when ready to move onto the Assignments tab.
Assign Users to the App
There are two different sections you can allocate users or groups to depending on how you want the app rolled out to users:
- Required = The app is MANDATORY for these users/groups. Any user or group in this section will have the App automatically pushed out to them.
- Available for enrolled devices = The app is OPTIONAL for these users/groups. The app will not be automatically pushed and the users can go to download the app themselves from within the Company Portal.
Assign your users or groups to the ZCC app accordingly.
Click Next to continue and then Create on the following screen. Your Line-of-Business application will be created and the MSI will upload - be sure to wait until it's complete.
Done!
This section will cover deploying ZCC onto macOS using Intune.
macOS requires a little bit more effort to get going than Windows does. We will need to do the following on a local macOS machine:
- Download the Zscaler Client Connector installer for macOS (this is a
.appfile) - Create a post-installation script (to customize the install of ZCC with our chosen arguments)
- Convert the .app file and script to .pkg (Intune can only work with pkg files on macOS)
- Wrap the .pkg file using the Intune App Wrapping Tool (creates an
.intunemacfile)
If you're using MacOS Catalina 10.15 or higher, you MUST use ZCC v2.1.X or above. Catalina introduced the requirement that apps are notarized by their developers. Only ZCC releases v2.1 and above are notarized by Zscaler.
Do I need an Apple Developer Account?
An Apple Developer Account is recommended.
You can proceed and deploy the agent without an Apple Developer account, however you will not be able to sign and notarize the .pkg file created below without a valid Developer ID. This will result in your users receiving an error about an the software coming from an ‘Unidentified Developer', and depending on security settings, the device may block the install altogether.
If you enroll in the Apple Developer program (US$99), you can sign and notarize your package which will make this error go away. If you're an organization running a macOS deployment, you will most likely have a developer account for the company already.
But shouldn't Zscaler have already signed the app I'm deploying?
Yes, Zscaler HAS both signed and notarized the .app package that will be installed. The problem with Intune is that it can only deploy .pkg files to macOS; NOT .app files. We need to wrap our .app file inside a .pkg file for it to work with Intune, and it is this pkg file that needs to be signed and notarized as well.
Obtaining Developer ID Certificates
To sign an notarize the .pkg, you will need both the Developer ID Installer and Developer ID Application certificates. You can create these under the Certificates, Identifiers & Profiles section of your developer account, but will need a Certificate Signing Request (CSR) to do so: Apple have a brief guide on how to generate one using Keychain, here.
Download the certificates when you have them and click to open the .cer files in Keychain. Add them as a login certificate.
You can check the certificates have been installed correctly by running the following command:
If you have the Developer ID Installer and Developer ID Application certificates, you're good to proceed.
1. Download the Zscaler Client Connector .app
To start, you'll need the .app installer for ZCC from the Zscaler Client Connector Portal.
Log into the portal (either through ZIA or ZPA) and navigate to Administration > Zscaler Client Connector Store.
In the macOS panel, click the download link for the latest 2.X.X version. Do not use the older 1.X.X releases.
Unzip the file downloaded to obtain the .app installer.
2. Create the post-installation script
Intune will push out and install the .pkg file - which is just our .app file wrapped up as a .pkg for the purposes of Intune deployment.
The problem is however, that when Intune deploys the .pkg, it just saves the wrapped .app to the user's device without doing anything else. We need a way to run and install the .appafter Intune has deployed the .pkg, PLUS a way to include arguments to customize the install. A post-installation script will do all of this for us.
To start, on a macOS device open Terminal:
Create a folder called scripts. Inside this folder, create a file called postinstall
Note down the full path to the scripts directory - we'll need this later.
Open the postinstall file for editing:
Copy and paste the following into the Terminal window (modify the arguments as required):
To exit Nano, press Control + X and then Y to save.
This will do a silent installation of the Zscaler Client Connector (unattended mode) and automatically redirect the user to your company SSO page to sign in.
Important! When entering the cloud name (--cloudName), DO NOT enter the .net at the end. Eg: zscalertwo.net should be entered as zscalertwo
Command-line arguments can be used for each platform to customize the install. For example, --strictEnforcement 1 can be used to block access to the internet until your users enroll in the Zscaler Client Connector.

For a list and description of all the .app customization options, scroll down to point #4 in this help article.
As an example, the script for my installation looks like the following:
Lastly, we need to make the script executable. Run the following in Terminal:
3. Create the PKG file
Intune only supports pkg files for macOS. A .pkg file is analogous to an MSI for Windows. All we are essentially doing is wrapping the .app file inside a .pkg file so that it can be deployed by Intune.
We'll be using the built-in pkgbuild tool to do this. Open Terminal and run the following command (change the file paths before running):
| Field | Description |
|---|---|
--install-location | This should point to the tmp folder, or somewhere writeable on the user machine. The .pkg will unpack itself here, then run the .app installer; which will install ZCC to the /Applications directory as required. If you change this from /tmp, you'll need to update the postinstall script as well. |
--scripts | This should be the path to the scripts folder you created in the step above. |
--component | This file path should point to the Zscaler Client Connector .app file you downloaded in Step #1. |
--identifier | Specify a unique identifier for this package. It is advisable to set a meaningful, consistent identifier, eg: com. zscaler. zscalerclientconnector |
--version | This has no relationship to the actual Zscaler Client Connector version. This is only used by Intune. If you ever deploy another pkg via Intune for a different version of ZCC, you'll need to increment this (eg: Version 1.1) so that Intune can tell the pkg files apart. Note that ZCC has its own update mechanism, so you don't need to worry about using Intune to push out updates to the Zscaler Client Connector software. |
--sign | If you don't want your users to recieve an error that your package is from an ‘Unidentified Developer' (which will prevent installation entirely), you will need to sign the package using a valid Apple Developer ID. To do this, you will need to enroll in the Apple Developer program (US$99). If you are an organization, you probably have already done this. Make sure you correctly substitute MY-DEV-NAME with your correct Developer name / org name. If you don't care about the ‘Unidentified Developer' error, you can remove the--signargument. |
Zscaler Download For Windows 10
The last file path listed points to the location where you want to save the output pkg file.
If you're signing the package and are not sure about your team / developer / org certificate name, you can check this under the Certificates, Identifiers & Profiles section of your Apple Developer account, here.
As an example, my completed pkgbuild command is below:
If you signed your package, you can validate the signatures using pkgutil:
For example:
4. Notorize the PKG
You only need to do this step if you signed the .pkg file in the previous step. Otherwise you can skip to the next step.
What is notarization? According to Apple:
Notarization gives users more confidence that the Developer ID-signed software you distribute has been checked by Apple for malicious components. If there are no issues, the notary service generates a ticket for you to staple to your software; the notary service also publishes that ticket online where Gatekeeper can find it.
Beginning in macOS 10.14.5, software signed with a new Developer ID certificate and all new or updated kernel extensions must be notarized to run. Beginning in macOS 10.15 [Catalina], all software built after June 1, 2019, and distributed with Developer ID must be notarized.
Create an App Specific Password
We're going to notarize the .pkg file via the command-line. To do this, you'll need to generate an App Specific Password for your the Apple ID of your Developer Account:
How to generate an app-specific password
- Sign in to your Apple ID account page.
- In the Security section, click Generate Password below App-Specific Passwords.
- Follow the steps on your screen.
Next, open Keychain and click the '+' icon to add a new Keychain Item.
- For Keychain Item Name, enter
notarization-tool - For Account Name, enter the email associated with your Developer Account / Apple ID.
- For Password, copy and paste the app-specific password from your Apple ID account.
Request Notorization
To request notarization from Apple, run the following command (replacing the values with your own):
| Field | Value |
|---|---|
username | The Apple ID username associated with your Apple Developer Account |
password | Enter @keychain: followed by the name of the Keychain Item which you saved your app-specific password to. This will fetch the password from the keychain. |
asc-provider | This is the Team ID from your Developer Account. You can find this by logging into your Developer Account and reviewing your profile |
primary-bundle-id | This should match the identifier you specified when you created the pkg. |
file | The path to the .pkg file |
For example:
If you receive an error that the tool is not on your machine, ensure you have Xcode and Xcode Command-line Tools installed.
The command will take a while to run as it is uploading your .pkg file to Apple. Once done, it will return a UUID which you can use to check the status of your notarization request:
Once the process is complete (mine took under 10 minutes), you'll recieve a confirmation email as to whether your request was successful or not.
Staple the Notorization Ticket
The last step is to staple the notarization ticket to the .pkg file. This ensures that a Mac device that is offline can still validate that the .pkg file is notarized:
Note: If your command fails, wait a few minutes and try again. If your command continuously fails, and your traffic is going through ZIA or another proxy, you may need to bypass api.apple-cloudkit.com from SSL inspection due to certificate pinning.

2. Add a new Line-of-Business App
Add a new Line of Business (LoB) App
Back in the Apps menu of the MEM portal, navigate to Apps > All Apps > Add. In the panel that appears, scroll to the bottom and under the Other heading, select Line-of-business app.
When prompted to select an app package file, upload the MSI of the Zscaler Client Connector you downloaded above and click OK.
Customize the App Details
Fill in the required details about the app:
| Field | Content |
|---|---|
| Name | Enter Zscaler Client Connector 2.X.X.X (where 2.X.X.X is the version number of the app - this will help you distinguish what version is being distributed by Intune) |
| Description | Enter Zscaler Client Connector |
| Publisher | Enter Zscaler, Inc |
| Ignore app version | Set to Yes. ZCC will automatically update itself once deployed, so Intune can safely ignore the version the user has installed after deployment. |
| Category | (Optional) Select an app category to allocate the Zscaler Client Connector to. |
| Command-line arguments | See below. |
For the Command-line arguments section, enter the following (substituting in your own cloud and domain info):
Important!
- When entering the cloud name, DO NOT enter the .net at the end. Eg: zscalertwo.net should be entered as
zscalertwo - All command-line arguments should be on a single line with a space separating them. Do not linebreak each argument or they will fail.
Command-line arguments can be used for each platform to customize the install. For example, STRICTENFORCEMENT can be used to block access to the internet until your users enroll in the Zscaler Client Connector.
For a list and description of all the MSI customization options, scroll down to point #5 in this help article.
Click Next when ready to move onto the Assignments tab.
Assign Users to the App
There are two different sections you can allocate users or groups to depending on how you want the app rolled out to users:
- Required = The app is MANDATORY for these users/groups. Any user or group in this section will have the App automatically pushed out to them.
- Available for enrolled devices = The app is OPTIONAL for these users/groups. The app will not be automatically pushed and the users can go to download the app themselves from within the Company Portal.
Assign your users or groups to the ZCC app accordingly.
Click Next to continue and then Create on the following screen. Your Line-of-Business application will be created and the MSI will upload - be sure to wait until it's complete.
Done!
This section will cover deploying ZCC onto macOS using Intune.
macOS requires a little bit more effort to get going than Windows does. We will need to do the following on a local macOS machine:
- Download the Zscaler Client Connector installer for macOS (this is a
.appfile) - Create a post-installation script (to customize the install of ZCC with our chosen arguments)
- Convert the .app file and script to .pkg (Intune can only work with pkg files on macOS)
- Wrap the .pkg file using the Intune App Wrapping Tool (creates an
.intunemacfile)
If you're using MacOS Catalina 10.15 or higher, you MUST use ZCC v2.1.X or above. Catalina introduced the requirement that apps are notarized by their developers. Only ZCC releases v2.1 and above are notarized by Zscaler.
Do I need an Apple Developer Account?
An Apple Developer Account is recommended.
You can proceed and deploy the agent without an Apple Developer account, however you will not be able to sign and notarize the .pkg file created below without a valid Developer ID. This will result in your users receiving an error about an the software coming from an ‘Unidentified Developer', and depending on security settings, the device may block the install altogether.
If you enroll in the Apple Developer program (US$99), you can sign and notarize your package which will make this error go away. If you're an organization running a macOS deployment, you will most likely have a developer account for the company already.
But shouldn't Zscaler have already signed the app I'm deploying?
Yes, Zscaler HAS both signed and notarized the .app package that will be installed. The problem with Intune is that it can only deploy .pkg files to macOS; NOT .app files. We need to wrap our .app file inside a .pkg file for it to work with Intune, and it is this pkg file that needs to be signed and notarized as well.
Obtaining Developer ID Certificates
To sign an notarize the .pkg, you will need both the Developer ID Installer and Developer ID Application certificates. You can create these under the Certificates, Identifiers & Profiles section of your developer account, but will need a Certificate Signing Request (CSR) to do so: Apple have a brief guide on how to generate one using Keychain, here.
Download the certificates when you have them and click to open the .cer files in Keychain. Add them as a login certificate.
You can check the certificates have been installed correctly by running the following command:
If you have the Developer ID Installer and Developer ID Application certificates, you're good to proceed.
1. Download the Zscaler Client Connector .app
To start, you'll need the .app installer for ZCC from the Zscaler Client Connector Portal.
Log into the portal (either through ZIA or ZPA) and navigate to Administration > Zscaler Client Connector Store.
In the macOS panel, click the download link for the latest 2.X.X version. Do not use the older 1.X.X releases.
Unzip the file downloaded to obtain the .app installer.
2. Create the post-installation script
Intune will push out and install the .pkg file - which is just our .app file wrapped up as a .pkg for the purposes of Intune deployment.
The problem is however, that when Intune deploys the .pkg, it just saves the wrapped .app to the user's device without doing anything else. We need a way to run and install the .appafter Intune has deployed the .pkg, PLUS a way to include arguments to customize the install. A post-installation script will do all of this for us.
To start, on a macOS device open Terminal:
Create a folder called scripts. Inside this folder, create a file called postinstall
Note down the full path to the scripts directory - we'll need this later.
Open the postinstall file for editing:
Copy and paste the following into the Terminal window (modify the arguments as required):
To exit Nano, press Control + X and then Y to save.
This will do a silent installation of the Zscaler Client Connector (unattended mode) and automatically redirect the user to your company SSO page to sign in.
Important! When entering the cloud name (--cloudName), DO NOT enter the .net at the end. Eg: zscalertwo.net should be entered as zscalertwo
Command-line arguments can be used for each platform to customize the install. For example, --strictEnforcement 1 can be used to block access to the internet until your users enroll in the Zscaler Client Connector.
For a list and description of all the .app customization options, scroll down to point #4 in this help article.
As an example, the script for my installation looks like the following:
Lastly, we need to make the script executable. Run the following in Terminal:
3. Create the PKG file
Intune only supports pkg files for macOS. A .pkg file is analogous to an MSI for Windows. All we are essentially doing is wrapping the .app file inside a .pkg file so that it can be deployed by Intune.
We'll be using the built-in pkgbuild tool to do this. Open Terminal and run the following command (change the file paths before running):
| Field | Description |
|---|---|
--install-location | This should point to the tmp folder, or somewhere writeable on the user machine. The .pkg will unpack itself here, then run the .app installer; which will install ZCC to the /Applications directory as required. If you change this from /tmp, you'll need to update the postinstall script as well. |
--scripts | This should be the path to the scripts folder you created in the step above. |
--component | This file path should point to the Zscaler Client Connector .app file you downloaded in Step #1. |
--identifier | Specify a unique identifier for this package. It is advisable to set a meaningful, consistent identifier, eg: com. zscaler. zscalerclientconnector |
--version | This has no relationship to the actual Zscaler Client Connector version. This is only used by Intune. If you ever deploy another pkg via Intune for a different version of ZCC, you'll need to increment this (eg: Version 1.1) so that Intune can tell the pkg files apart. Note that ZCC has its own update mechanism, so you don't need to worry about using Intune to push out updates to the Zscaler Client Connector software. |
--sign | If you don't want your users to recieve an error that your package is from an ‘Unidentified Developer' (which will prevent installation entirely), you will need to sign the package using a valid Apple Developer ID. To do this, you will need to enroll in the Apple Developer program (US$99). If you are an organization, you probably have already done this. Make sure you correctly substitute MY-DEV-NAME with your correct Developer name / org name. If you don't care about the ‘Unidentified Developer' error, you can remove the--signargument. |
Zscaler Download For Windows 10
The last file path listed points to the location where you want to save the output pkg file.
If you're signing the package and are not sure about your team / developer / org certificate name, you can check this under the Certificates, Identifiers & Profiles section of your Apple Developer account, here.
As an example, my completed pkgbuild command is below:
If you signed your package, you can validate the signatures using pkgutil:
For example:
4. Notorize the PKG
You only need to do this step if you signed the .pkg file in the previous step. Otherwise you can skip to the next step.
What is notarization? According to Apple:
Notarization gives users more confidence that the Developer ID-signed software you distribute has been checked by Apple for malicious components. If there are no issues, the notary service generates a ticket for you to staple to your software; the notary service also publishes that ticket online where Gatekeeper can find it.
Beginning in macOS 10.14.5, software signed with a new Developer ID certificate and all new or updated kernel extensions must be notarized to run. Beginning in macOS 10.15 [Catalina], all software built after June 1, 2019, and distributed with Developer ID must be notarized.
Create an App Specific Password
We're going to notarize the .pkg file via the command-line. To do this, you'll need to generate an App Specific Password for your the Apple ID of your Developer Account:
How to generate an app-specific password
- Sign in to your Apple ID account page.
- In the Security section, click Generate Password below App-Specific Passwords.
- Follow the steps on your screen.
Next, open Keychain and click the '+' icon to add a new Keychain Item.
- For Keychain Item Name, enter
notarization-tool - For Account Name, enter the email associated with your Developer Account / Apple ID.
- For Password, copy and paste the app-specific password from your Apple ID account.
Request Notorization
To request notarization from Apple, run the following command (replacing the values with your own):
| Field | Value |
|---|---|
username | The Apple ID username associated with your Apple Developer Account |
password | Enter @keychain: followed by the name of the Keychain Item which you saved your app-specific password to. This will fetch the password from the keychain. |
asc-provider | This is the Team ID from your Developer Account. You can find this by logging into your Developer Account and reviewing your profile |
primary-bundle-id | This should match the identifier you specified when you created the pkg. |
file | The path to the .pkg file |
For example:
If you receive an error that the tool is not on your machine, ensure you have Xcode and Xcode Command-line Tools installed.
The command will take a while to run as it is uploading your .pkg file to Apple. Once done, it will return a UUID which you can use to check the status of your notarization request:
Once the process is complete (mine took under 10 minutes), you'll recieve a confirmation email as to whether your request was successful or not.
Staple the Notorization Ticket
The last step is to staple the notarization ticket to the .pkg file. This ensures that a Mac device that is offline can still validate that the .pkg file is notarized:
Note: If your command fails, wait a few minutes and try again. If your command continuously fails, and your traffic is going through ZIA or another proxy, you may need to bypass api.apple-cloudkit.com from SSL inspection due to certificate pinning.
Validate the staple action was successful:
5. Test the PKG
Before going further, test your PKG file by running it and seeing if it successfully installs the Zscaler Client Connector silently. Make sure you don't already have ZCC installed when doing this however!
If you have an existing installation of ZCC, you can remove it under Applications/Zscaler/Uninstall-Zscaler-App
6. Create an .intunemac file
Once you've verified your PKG file functions correctly, we need to wrap it for use with Intune.
Zscaler App Download Windows 10
Download the Intune App Wrapping Tool for Mac (this is a Microsoft-owned repository).
Next:
- Unzip the source code folder
- Open Terminal
- Change directory to where the
IntuneAppUtilfile is located - Make the
IntuneAppUtilfile executable:
Locate the PKG file you created above and use the IntuneAppUtil tool to wrap the .pkg file to a .intunemac file:
For example:
If everything went well, you should see the .intunemac file in your specified output directory.
7. Add a new Line-of-Business app in MEM
Add a new Line of Business (LoB) App
In the Apps menu of the MEM portal, navigate to Apps > All Apps > Add. In the panel that appears, scroll to the bottom and under the Other heading, select Line-of-business app.
When prompted to select an app package file, upload the.intunemacfile you created above and click OK.
Customize the App Details
Fill in the required details about the app:
| Field | Content |
|---|---|
| Name | Enter Zscaler Client Connector 2.X.X.X - macOS 2.X.X.X (where 2.X.X.X is the version number of the app - this will help you distinguish what version is being distributed by Intune) |
| Description | Enter Zscaler Client Connector for macOS |
| Publisher | Enter Zscaler, Inc |
| Minimum operating system | Select OS X Yosemite 10.10 (ZCC supports macOS 10.10+) |
| Ignore app version | Set to Yes. ZCC will automatically update itself once deployed, so Intune can safely ignore the version the user has installed after deployment. |
| Category | (Optional) Select an app category to allocate the Zscaler Client Connector to. |
Click Next to move to the Assignments tab.
Assign Users to the App
There are two different sections you can allocate users or groups to depending on how you want the app rolled out to users:
- Required = The app is MANDATORY for these users/groups. Any user or group in this section will have the App automatically pushed out to them.
- Available for enrolled devices = The app is OPTIONAL for these users/groups. The app will not be automatically pushed and the users can go to download the app themselves from within the Company Portal.
Assign your users or groups to the ZCC app for macOS accordingly.
Zscaler Mac Install
Click Next to continue and then Create on the following screen. Your macOS Line-of-Business application will be created and the .intunemac file will upload - be sure to wait until it's complete.
Zscaler Client Connector Download
Done!

